Malicious Android App: While the Google Play Store has millions of beneficial Android applications and games, it also contains malicious apps that represent a privacy risk to users. A new harmful App has been identified that can carry the “TeaBot” banking malware, which is meant to steal sensitive user data such as passwords, bank credentials, and text messages from your Android phone. Let’s take a closer look at the specifics down below.
TeaBot is a banking Trojan horse. QR Code App was used to find it
TeaBot, also known as Toddler and Anatsa, is a banking trojan that was first spotted in May 2021. It was targeting European banks at the time, stealing two-factor authentication (2FA) tokens supplied via text messages. However, according to research published by Cleary, malware and online fraud protection platform, the virus has developed and is now being used to target people in Russia, Hong Kong, and the United States.
(also see: How To Keep Smartphone Safe From Cyber Attacks)
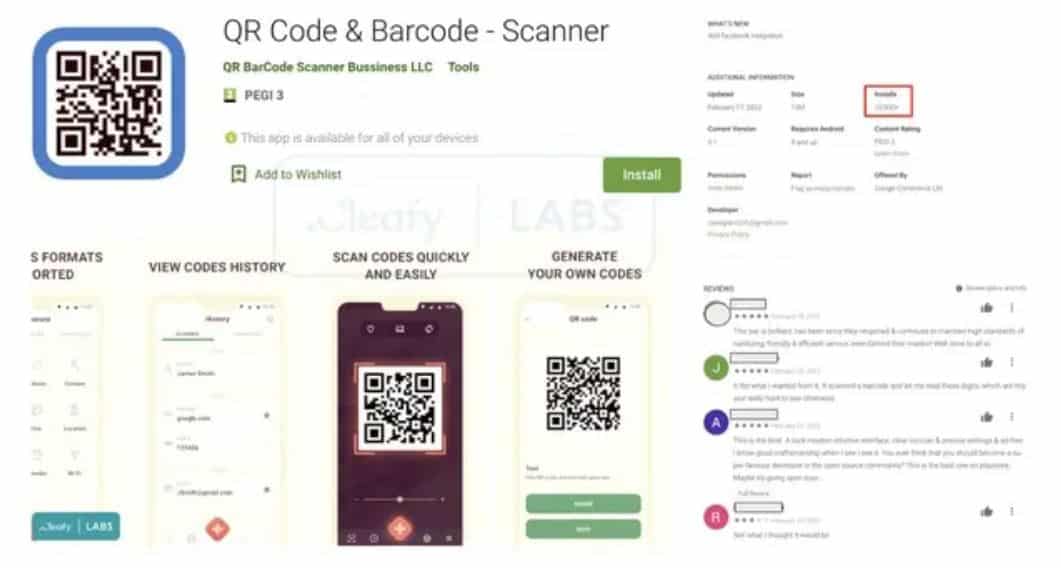
According to the research, the Android app “QR Code & Barcode — Scanner” was the most recent TeaBot-laden app in the Google Play Store with over 10,000 downloads. While the programme appeared to be authentic at first sight, it sought permission to download a second “QR Coder Scanner: Add On” application, which featured the TeaBot samples when it was downloaded.
After installing the second app, it requested permission to see and control the device’s screen to get sensitive user data such as SMS, login credentials, and 2FA codes. Furthermore, the trojan, like other banking viruses, captured the user’s keyboard keystrokes to extract sensitive information.
Because the QR Code & Barcode – Scanner application appeared to be real, the majority of user evaluations were favorable. Furthermore, the app downloads the TeaBot malware as an in-app update, making it “nearly undetected” by many Android antivirus solutions.
“Since the dropper application distributed on the official Google Play Store requests only a few permissions and the malicious app is downloaded at a later time, it is able to get confused among legitimate applications and it is almost undetectable by common antivirus solutions,” Cleafy researchers wrote in their report.
Previously, the TeaBot malware was propagated via SMS phishing campaigns that enticed users with popular Android apps such as VLC Media Player, TeaTV, DHL, or UPS. These apps operated as a “dropper” for the harmful TeaBot trojan, which means they seemed to be legitimate apps but delivered a second-stage malicious payload that installed TeaBot on customers’ devices.
While Google has already banned the QR Code & Barcode – Scanner from the PlayStore, Cleafy adds that TeaBot is now targeting 400+ Android applications. Crypto wallets, insurance applications, and home banking apps are examples of these. So, if you use an Android device, especially if you live in Hong Kong, Russia, or the United States, be wary of the TeaBot virus on the Google Play Store! Malicious Android Apps.
Via: Techcrunch